In case we want to monitor internet traffic generated or is generating in LAN, here is a detailed process how we can do it with Colasoft protocol analyzer – Capsa.
Again we must make sure the protocol analyzer software is correctly implemented so we can capture all the traffic in LAN, if you don’t know how to do it, please make sure you read how to implement a protocol analyzer.
First let’s launch a new project with Colasoft protocol analyzer, then do some online activities, such as chatting, browsing a website, sending and receiving emails, downloading some files. All these activities will generate different kinds of internet traffic. We may keep the project running to continuously monitor internet traffic or stop the project to do some analysis.
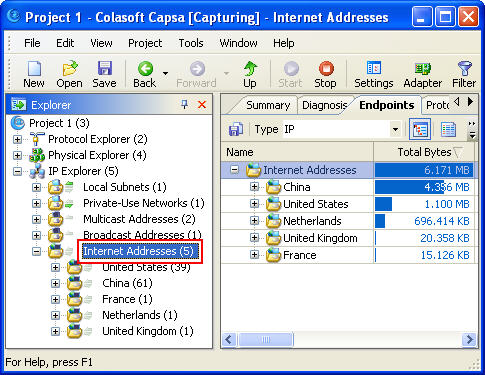
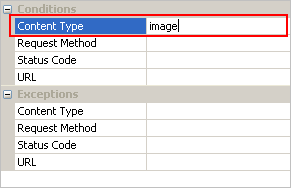
To monitor internet traffic, we’d better first select the “Internet Addresses” in the “Explorer” on the left window:
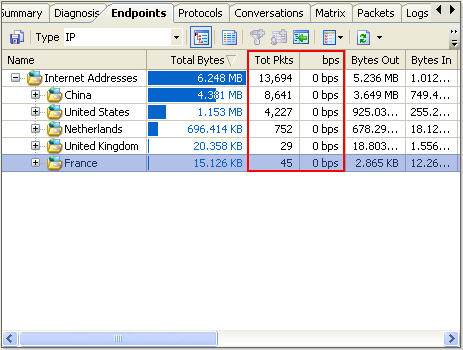
We can see that all the internet addresses are listed by countries, to monitor internet traffic of a specific country, we just need click on it; If we want to monitor internet traffic of a specific IP address within one country, we need to expand the country node and select the IP address in it.
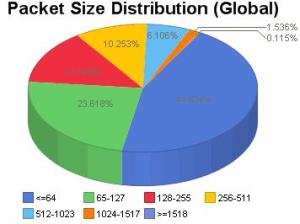
Also we can monitor internet traffic aggregated or internet traffic in real-time
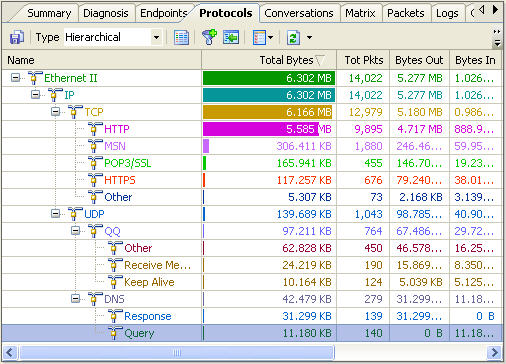
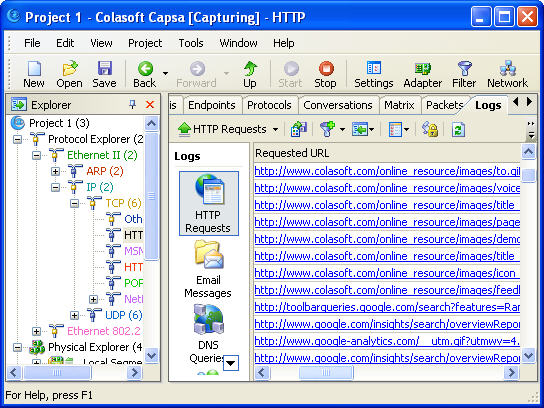
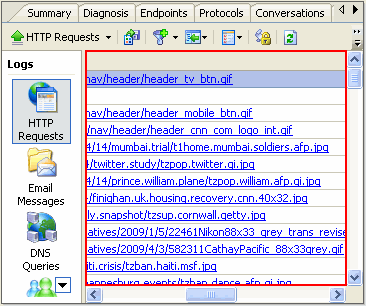
To view what online activities have generated or are generating internet traffic, we need to use the “Protocols” Tab.
We can see there are protocols which separately stand for different internet activities:
HTTP – Website browsing
MSN – online chatting with Live Messenger
POP3 – Email
HTTPS - Website browsing via a secure link
QQ- online chatting with QQ
DNS – Domain Name System
About Capsa
Colasoft Capsa is a network analyzer (protocol analyzer or protocol analyzer) designed for network monitoring and troubleshooting. It performs packet capturing, network monitoring, protocol analyzing, packet decoding, and automatic diagnosing. By giving users insights into all of network's operations, Capsa makes it easy to isolate and solve network problems, identify network bottleneck and bandwidth use, and detect network vulnerabilities. Learn more about Capsa, please visit http://www.colasoft.com/capsa/